You’ll ned to pfSense boxes.
On our example we have both connected to INTERNET each one with one public access on the WAN interface.
For the LAN we’ve set up 2 class C networks. Let’s call pfSenseA the one using 10.110.8.1 (as LAN), and pfSenseB the one using 10.110.9.1.
First, Go to System -> Advance Options and Enable Secure Shell. We’ll connect to one of the boxes in order to create CA certificates.
We’ll start working on pfSeseB which is going to be our SERVER.
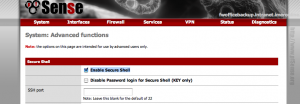
Enable Secure Shell
And then SSH to the box.
> ssh admin@10.110.9.1
You’ll be presented with the Console options:
*** Welcome to pfSense 1.2-RELEASE-embedded on fwofficebackup ***
OPT1(DMZ) -> rl0 -> NONE
LAN* -> rl1 -> 10.110.9.1
WAN* -> rl2 -> 67.63.42.4
pfSense console setup
***********************
0) Logout (SSH only)
1) Assign Interfaces
2) Set LAN IP address
3) Reset webConfigurator password
4) Reset to factory defaults
5) Reboot system
6) Halt system
7) Ping host
8) Shell
9) PFtop
10) Filter Logs
11) Restart webConfigurator
12) pfSense PHP shell
13) Upgrade from console
Enter an option:
Just option 8 (shell).
If you mounted disk is read-only move to another-one with rw privileges like “/tmp”
Then create a Shared Key
> openvpn –genkey –secret shared.key
copy it to the pfSense as follow:
>cat shared.key
and Copy the output.
Now, let’s go to pfSenseA and Click on VPN -> OpenVPN and ADD (+) an new Server:
- Add a Server OpenVPN
Let’s Create a TCP one, and copy the pasted key from the shell to the Share Key Field.
Add a Pool of unused addresses, in our example we’ll use 192.168.70.0/24 and for Remote Network use the net for pfSenseA, in our case 10.110.8.0/24
And we SAVE the changes on the pfSenseA
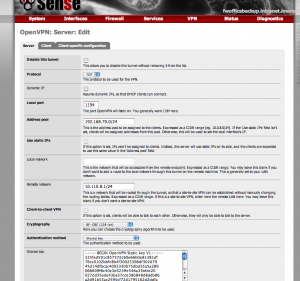
- Server
Now, on pfSenseA, will go to VPN->OpenVPN and we create a Client.
Configure the protocol as TCP and copy the SAME shared key we used on the server-side
As Server Address enter the PUBLIC IP address of pfSenseB.
As Remote IP use pfSenseB network 10.110.9.0/24 and for Interface IP use the pool of addresses you used on the Server-side (192.168.70.0/25)
NOTE. the attached image has the wrong IP Interface address, I’ve troubleshoot it at a later time.
And SAVE it.
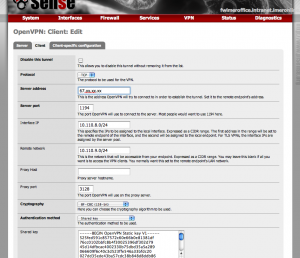
Client
Make sure that you allow incoming TCP to the OpenVPN port on both ipSense comming from each other.
Now ping from one network to the other, and DONE.





Nice post u have here 😀 Added to my RSS reader
I really like it here vpn,the best choise for Wi-fi navigation.
I entrusted him myr safety.
And the price is very good. I advise all to use it.
excellent post about open vpn